Bulletproof your network and your reputation with NeQter Labs.
Your best defense against internal and external threats is also your fast-track to cybersecurity compliance.
Created by defense contractors needing to protect sensitive technical information, the NeQter Compliance Engine is the ultimate plug-and-play solution for network-wide visibility and control, protecting proprietary information and enhancing your cybersecurity posture.

NeQter is created for small businesses, offering the fastest and most economical path to network security compliance. Through the use of a single unified appliance, NeQter helps achieve compliance with NIST SP 800-171 requirements and the impending Cybersecurity Maturity Model Certification (CMMC) requirements. It works immediately with your existing systems and network, helping to streamline the path to compliance. Further, it has embedded compliance expertise and cybersecurity best practices, pre-configured to demystify compliance for small businesses.
Security Information and Event Management (SIEM)
If your network is compromised, how would you know it?
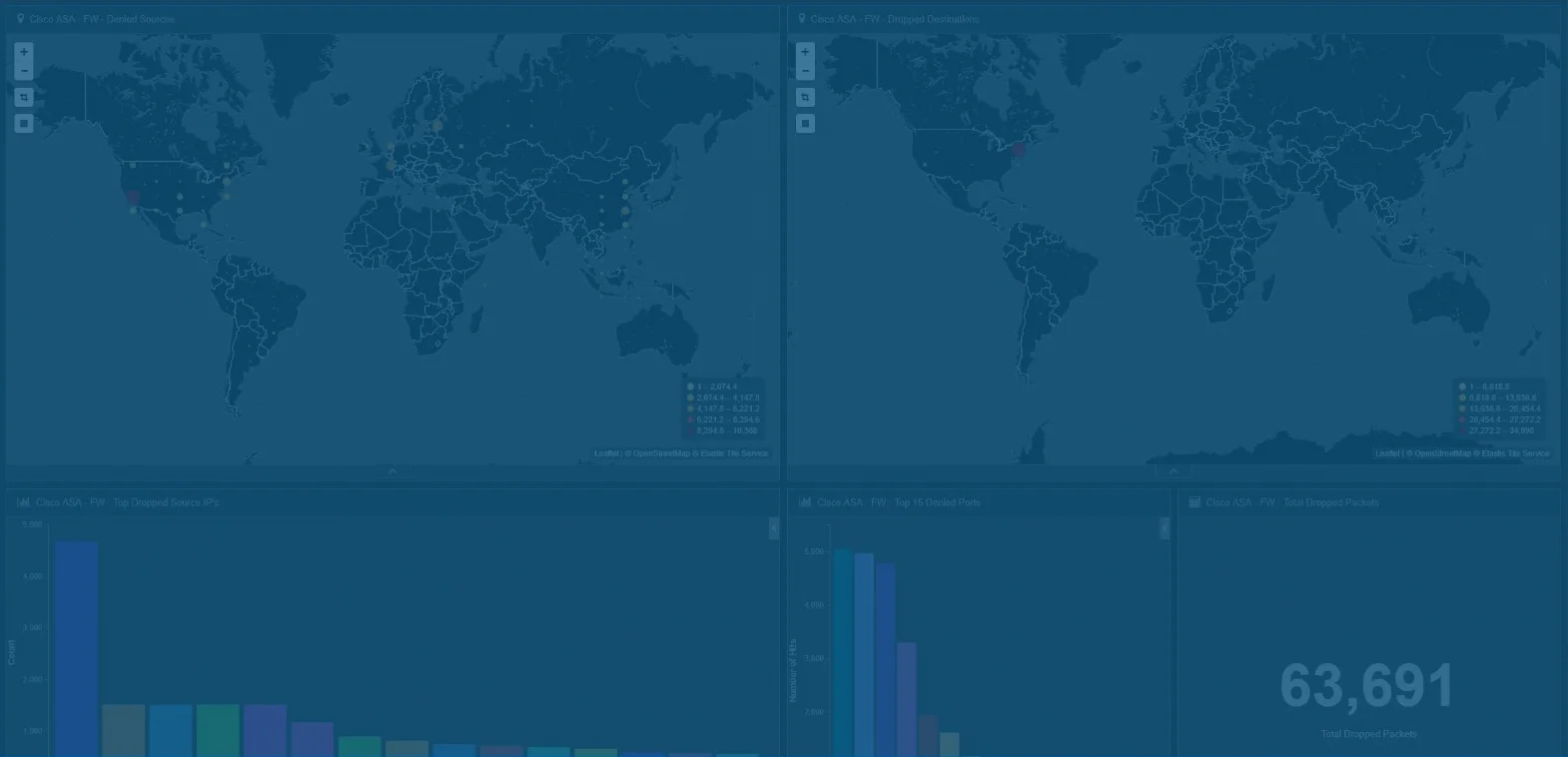
Know what is going on in your network, at any given time—whether a rogue employee has malicious intent or an unassuming employee shares sensitive information or an adversary has found a loophole into your network. More importantly, turn your logs into a format that allows you to take action.
For many companies, integrating a SIEM tool, configuring data streams from all devices, parsing the data, building useful dashboards, and knowing what all of the information actually means seems overwhelming.
NeQter’s plug-and-play SIEM system features:
- Prebuilt, intuitive dashboards to visualize useful information and make it easy to interpret data, identify trends and isolate anomalies—no technical background needed
- Pre-built alerts and options to customize notifications to your preferences
Out-of-the-Box Integration
The NeQter Compliance Engine seamlessly integrates with major firewall and software platforms including SonicWall, Synology, Cisco, Meraki, GSuite, Sophos, Cisco, WatchGuard, Fortinet, Barracuda
Always-On Monitoring
Know what’s happened, and prove it.
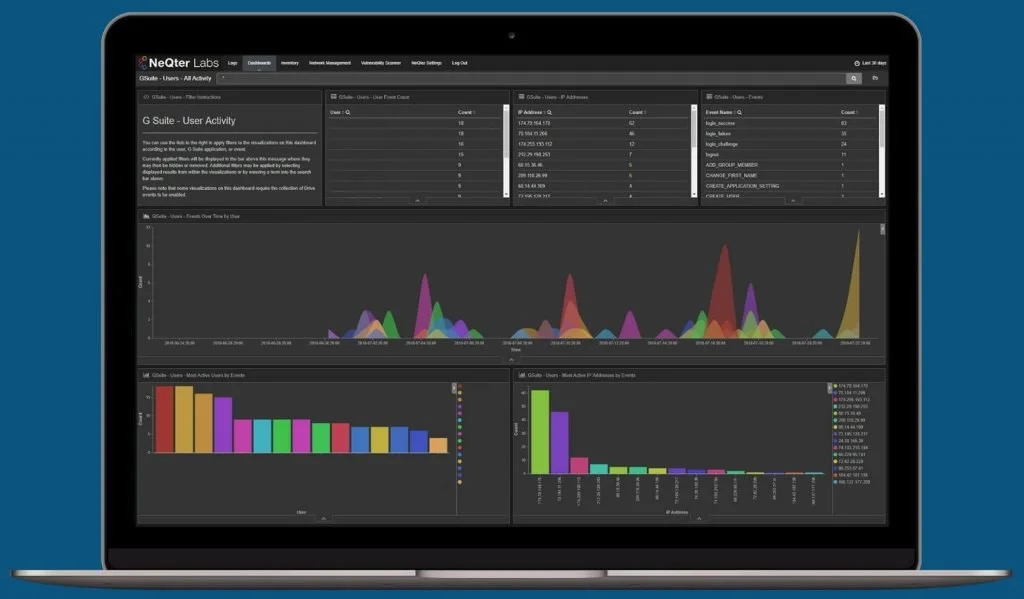
Threats and compromises can surface in many forms, and without proper vigilance, could go undetected for months… or even indefinitely.
The NeQter Compliance Engine provides continuous monitoring and alerts, including:
User Activity Monitoring
See when users log-on to your network, the type of device they use and any failed login attempts, for domain-level tracking. If you have web filtering, you can also track internet activity.
Endpoint Monitoring
See event logs at the local system or workstation level.
Cloud Service Monitoring
Track user login activity, file activity and file sharing with data in the cloud. Identify suspicious activity, view privilege changes, and understand when your files are shared within and outside the company.
File Activity Tracking
Know exactly who is accessing your intellectual property and CUI, and what they’re doing with it. You’ll know when files are deleted, moved or modified and who had access to them when it happened.
Vulnerability Scanning
Find and close loopholes… before attackers find them.
Bots. Hackers. Blackhats. They surface new vulnerabilities every day, to be exploited by attackers to infiltrate your network. Most software companies deploy patches in the hopes that you’ll update your systems and stay protected. NeQter’s automated vulnerability scanning does it for you.
NeQter’s vulnerability scanning is the first step in understanding the health of your network:
- Identifies vulnerabilities on the assets in your network
- Lists vulnerabilities by severity
- Recommends remediations, mitigations or workarounds
- New definitions are updated daily, so you’ll always have the latest information.
- Runs and compares reports for a clear audit trail
Inventory Management
What you can see, you can control.
NeQter automatically audits your network every 24 hours, creating an always up-to-date record of:
- All connected devices and drives
- All software installed on those devices
- Domain users and IPs associated with those devices
- All hardware specs and serial numbers
- Available and used hard drive space
Embedded Cyber Best-Practice Guidance and Templates
Demystify compliance with policy and plan wizards.
The NIST Cybersecurity Guidelines are broadly accepted as a “gold standard” but can be complicated to understand and implement. Built-in tools guide you through the requirements and help you create your tailored policies and plans—and implement them.
As your system of record, the NeQter Compliance Engine will guide your journey:
- Create your System Security Plan (SSP) and Plan of Actions and Milestones (POAM)
- Best-practice guidance to build policies tailored to your organization and work
Ready to protect your business, achieve compliance and win and retain contracts?
NeQter is the fastest, most comprehensive way to defend your business reputation, protect your customers’ proprietary information and achieve NIST SP 800-171 compliance.
Talk to us today, and let’s explore what Dostal Security & NeQter Labs can do for your organization.



