
Advanced File Encryption Software
Traditional IT controls focus on locking down networks, devices, and people. All of this is done in the name of protecting data. But, once individual files are moved, shared, or stolen, the data is no longer protected. Even worse, these controls get in the way and frustrate business users to the point they intentionally work around them. Anchor’s encryption tool inverts the equation by baking protection into the data, invisible to the business users (like antivirus), so that files are free to travel (even on mobile devices) and security is out of the way.
85%
Employees admitted taking company documents
78%
Internal data theft motivated by financial gain
80%
Ransomware attacks in 2021 involving exfiltration of data
How to anchor?
Protect your data in 3 simple steps
Anchor’s encryption process exists to make data security easy, and collaboration safe.

Choose what you want to protect

Pick who gets access

Select how it can be accessed
What is Anchor?
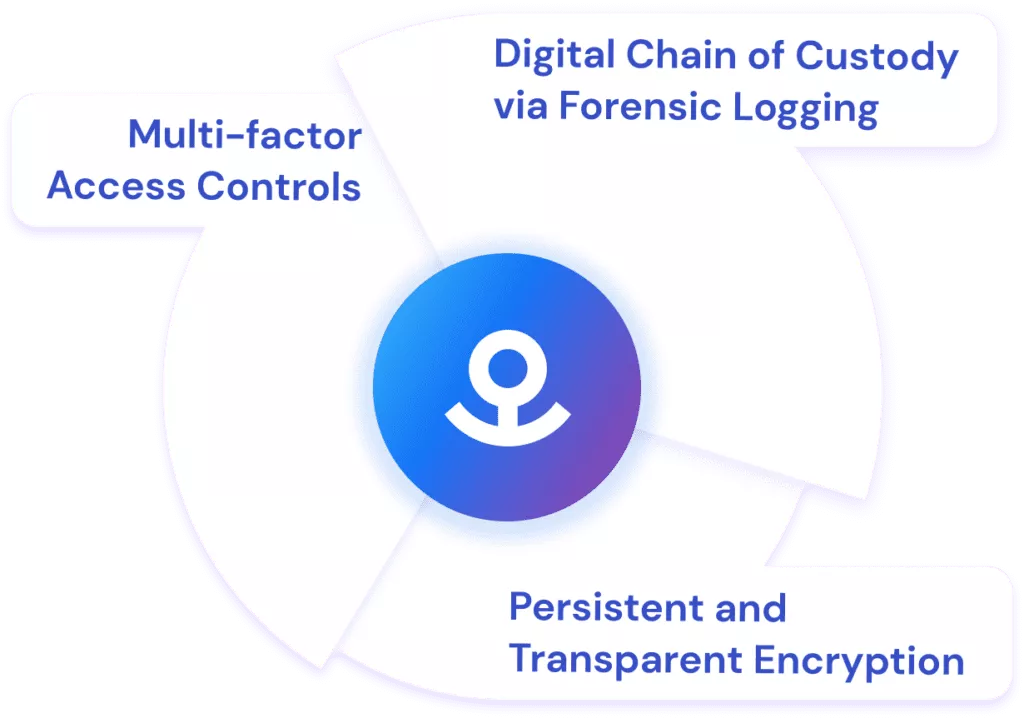
Patented combination of 3 well-known technologies
Persistent and Transparent Encryption
Anchored data is self–protecting. Each Anchored file is individually FIPS-validated encrypted at rest, in transit, and even while in use (saving does not generate plain text). Even if the files are stolen, they would never be more than cypher text due to our encryption process. Anchor uses Advanced Encryption Standard (AES) 256-bit military-grade encryption to provide a high level of encryption.
Multi-factor Access Controls
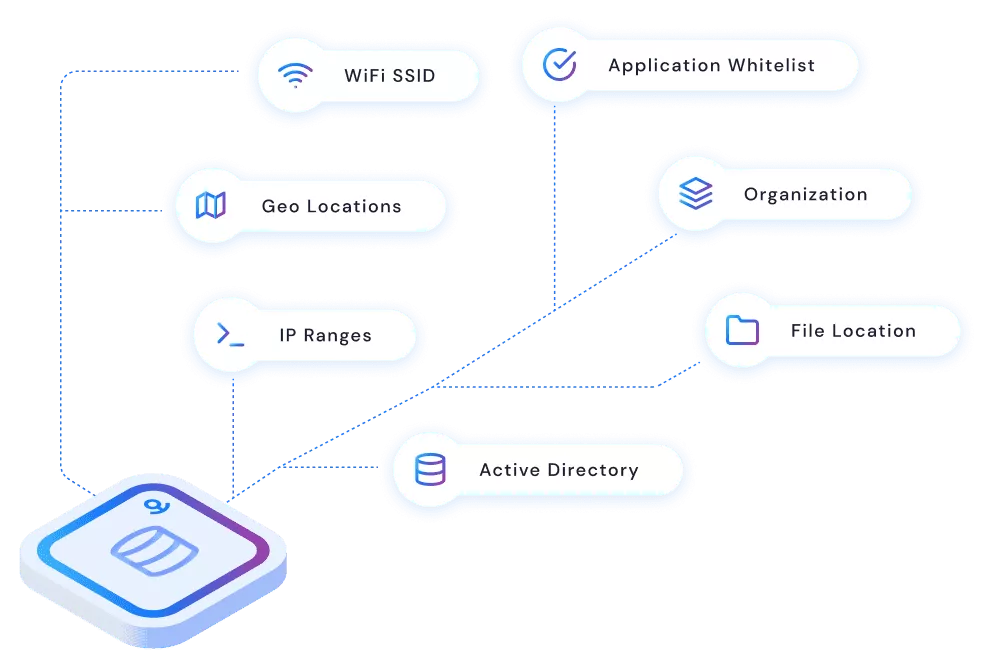
Patented heartbeat technology constantly verifies access rules in real-time based on a myriad of data sources such as Active Directory, geo-location, etc. When an access rule is broken, Anchor instantly revokes access. Even while the file is in use. Trust is never assumed, even after a file is open. Encryption software at its best.
Digital Chain of Custody via Forensic Logging
Real-time tracking of sensitive data. Audit trails of each request, including physical location. A true chain of custody for digital data.
Zero Trust Data Security
The world is connected and distributed. Data lives in the cloud and on IoT devices. Employees are working remotely and bringing their own devices. Bad actors are already inside the network. Networks and computers are no longer in the circle of trust. A zero-trust architecture (ZTA) is now the only way to be secure and have truly secure storage.
Anchor changes the game by shifting the paradigm from complex infrastructure security to simple individual file security. Our file encryption software actually eases the administrative burden while providing stronger protection for your sensitive data.
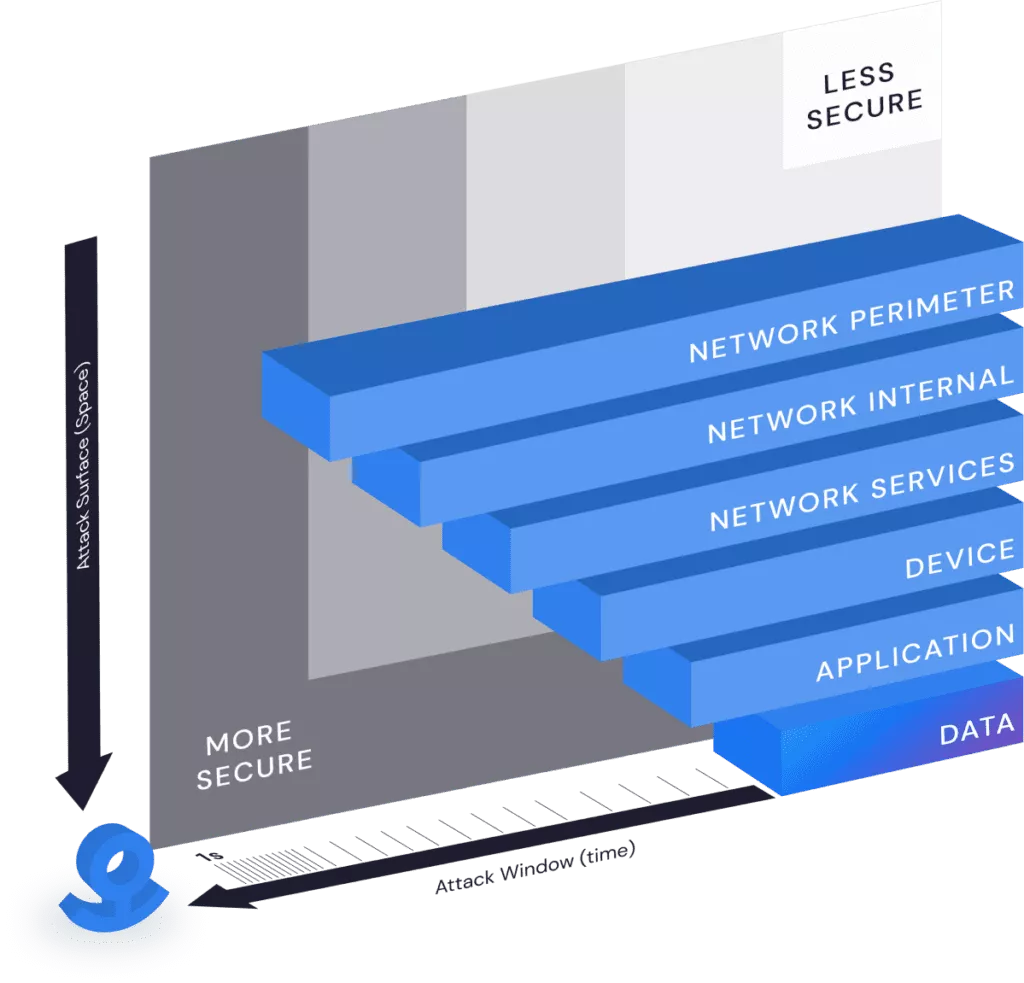
A Fortress for Every File
Zero trust architectures define micro-perimeters around protected resources in order to reduce the incentives and minimize the impact of a network breach. Anchor’s advanced encryption technology brings micro-perimeters to the file and removes the network from the equation entirely. With Anchor, every single file has its own independent security perimeter and every single request to use it is verified.
Continuous Authorization & Instant Revocation
Zero trust principles dictate that policies should be dynamic, based on as many sources of data as possible. Anchor brings zero trust authorization to files. Patented heartbeat technology constantly verifies access rules in real-time based on a myriad of organizational and contextual data sources such Active Directory, Geo-IP, IP address, Wi-Fi network, and more. It’s multi-factor authorization for file access. When an access rule is broken on a file in use, Anchor instantly shuts it down. Trust is never assumed, even after a file is open. Encryption software at its best.
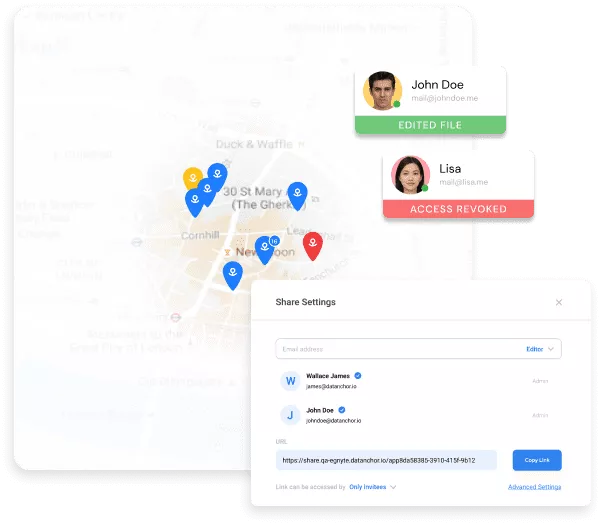
Share Access, Keep Control
Businesses share files to collaborate with others and create value. Too often, the recipients of that information misuse or abuse that data by leaving it unprotected, permanently retaining the information, or sharing it with unauthorized parties. Anchor is a lightweight solution that enforces zero trust security at the file level, based on the user, their role, and the context in which they’re trying to access data. It continues to protect and work with files outside an organization’s network just as well as it works inside, whether they have been shared or stolen. Anchor facilitates remote work and collaboration across the internet while maintaining strong protection against unauthorized data access. The perfect encryption software tool for today’s remote workforce.
Stop the Bad Guys, Not the Business
All over the world, businesses are increasingly under attack every day. In response to the ever-advancing threat organizations create more layers of security, via complex encryption programs, increasing the burden on the employees. This results in employees finding ways to circumvent those controls. Remember when password complexity requirements caused employees to write down their passwords and hide them under their keyboards?
Anchor protection is transparent to the end users and requires no workflow changes to how you use your applications today. The only time an end user is aware of the protection is when they use data in a way they are not allowed, like from a home computer.
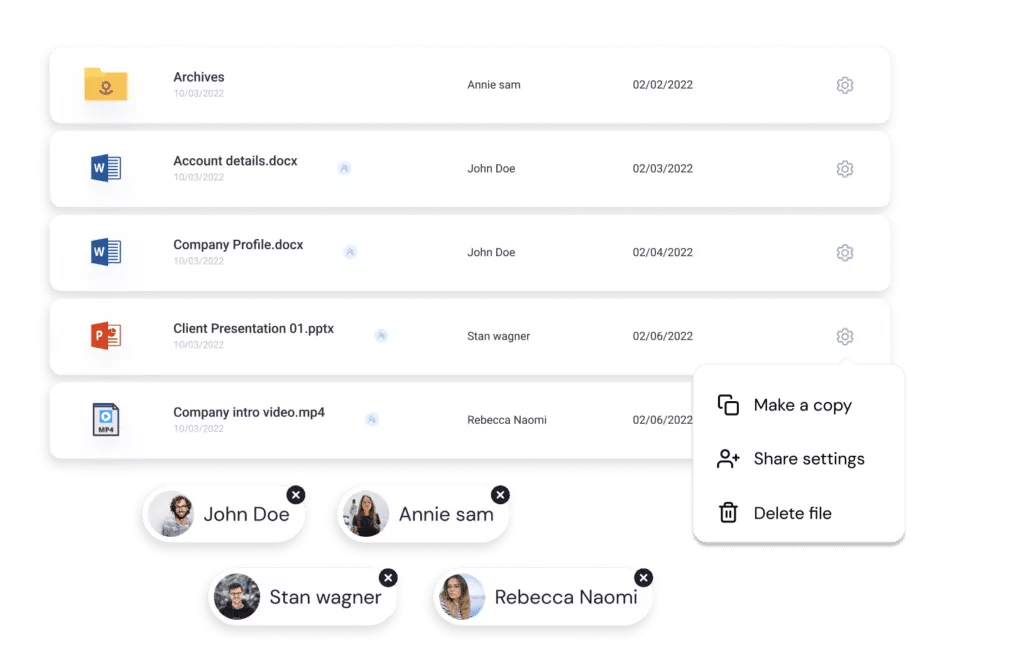
Control the data. Free the people.
Anchor is Simple, Transparent, and Affordable. Click “Get Started” below to see for yourself, in a matter of minutes. Or, if you prefer, click the link below to schedule a demo with our team.